



Track Visual Employee Activity Log
with Screenshots Monitoring
Get a visual log of what your employees are doing in real time with the remote screenshot capture feature. A great way to check in on your teams, in the modern workplace- office and remote, without interrupting them.
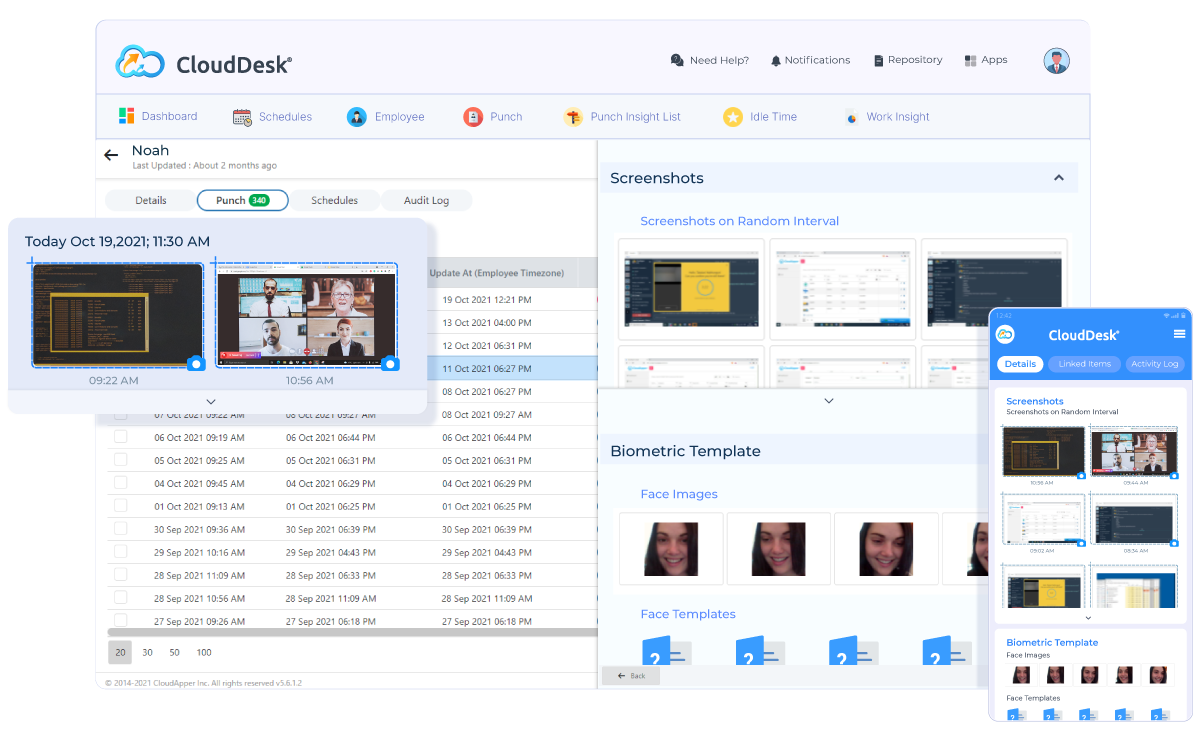

Captures and keep log of screenshots at specified/random intervals

Seamlessly captures screenshots throughout multi-screen PC setups

Spot suspicious activity and insider threat with visual proof of activity
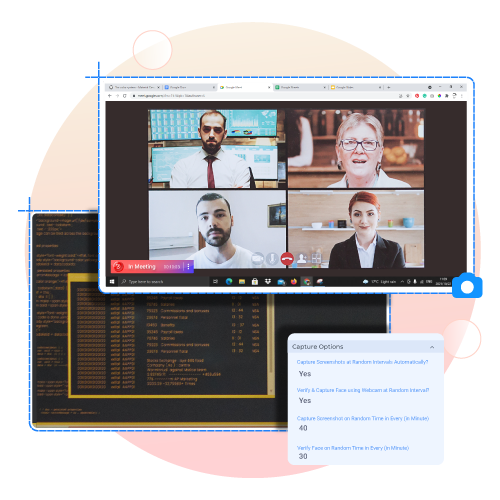
Best Employee Monitoring Software
with Screenshot Capturing Feature

Visualize work in progress
Gain visibility to analyze and customize productivity objectives for each individual for their assigned tasks/ projects.

Clearer picture of the workflow
Screenshots give you a better understanding of employee workflow, letting you know how each team member is executing their day to day tasks, to the goals you've set.

Less wasted time
Screenshot monitoring holds employees accountable about their task completion time, which results in increased productivity and efficiency.

Objective measurement of activity
It is hard to address an unproductive employee without any visual proof. Screenshots bring objectivity, accountability and a lot of clarity to address such issues.

Perfect for remote employees
Get visual insights on project progress across distributed team members to precisely predict, adjust, and manage projects and finish them within deadline.

Identify and secure sensitive data
No organization is fully immune to threats from harmful activity. Discover and identify suspicious visual activity to protect your most critical data.